
Home » Latest Articles » CAASM Use Case #1 – Find and fix missing device agents use case for cybersecurity observability with SJULTRA and CAASM

Hey there, fellow cybersecurity practitioners! This post is part of a series on Cybersecurity Observability use cases. This is use case 1 of 14 about finding and fixing devices with no security agent on them.
You know how it goes. The CSO owns the cybersecurity policies and has a “trust by verify” approach… so they sometimes wonder:
How do I know if we're actually implementing this security policy... I trust my team, but how can I verify it across our entire IT estate?
(Chief Security Office)Chief Security Officer
This is where cybersecurity observability comes in handy. It’s how to make sure all those policies aren’t just collecting “digital dust” in an IT policy document that nobody reads.
Let’s say you’ve got a simple policy that madates: All Windows devices must have the Carbon Black agent installed.
Sounds straightforward, right? But here’s the kicker – how do you make sure it’s happening for real? Can you account for all your agents in the field?
You're the Vulnerability and Patch Management Analyst who's trusted to enforce this policy. But you've got two major headaches: our CMDB isn't reliable, and our agents can tell us about devices they don't know about!
John Doe
Now, I don’t know about you, but that sounds like a recipe for some serious security gaps to me… 😭
This is where I get a bit excited, because I’ve been dealing with this challenge for over 20 years across many organizations, so it’s a relief to find a consistent and reliable solution to it.
At SJULTRA, with our customers we use this cool tool in our CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More Services to gather intel from multiple data sources.
It’s like having a super-spy network for your IT environment. CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More takes all this data from various collectors, adapters, systems, and devices, and turns it into actionable signals.
It’s like finding the security needle in the IT haystack!
Once we’ve got CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More set up (which, by the way, SJULTRA offers a free 30-day trial for), the fun begins. We can start building queries to find those elusive devices that are dodging our security measures.
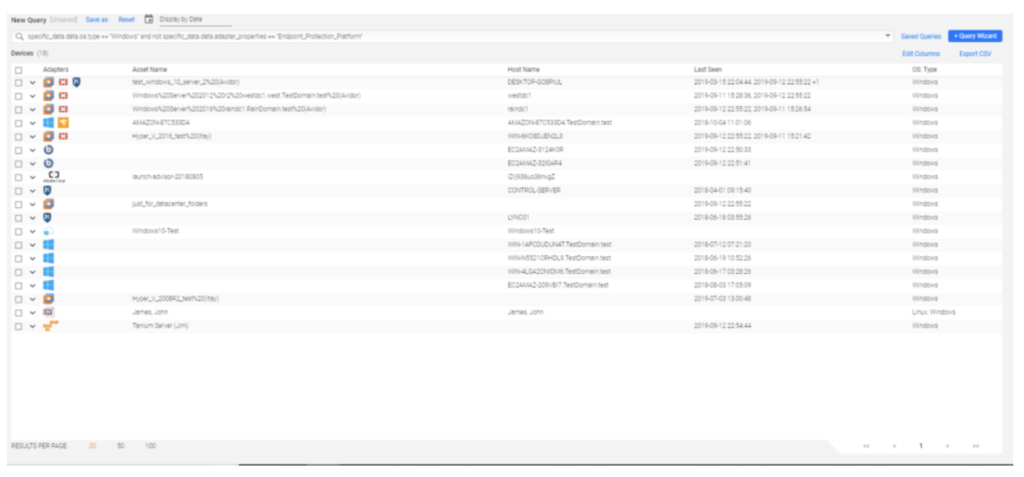
Want to find all Windows devices without the Carbon Black agent? No problem! Here’s how we do it:

(specific_data.data.os.type == "Windows") and not ((adapters_data.carbonblack_defense_adapter.id == ({"$exists":true,"$ne":""})))
I know, I know, it looks like a cat walked across the keyboard. But trust me, this little line of code is cybersecurity gold.
Result:
Feeling fancy? 😜 We can extend our query to get even more specific.
How about finding all Windows devices running Google Chrome without the Carbon Black agent? Here’s what that looks like:
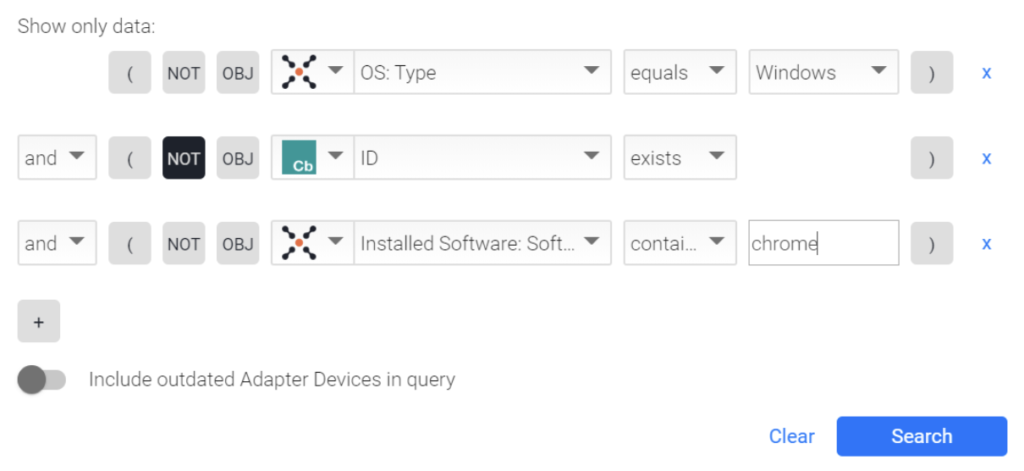
In AQL:
(specific_data.data.os.type == "Windows") and not ((adapters_data.carbonblack_defense_adapter.id == ({"$exists":true,"$ne":""}))) and (specific_data.data.installed_software.name == regex("chrome", "i"))
Result:
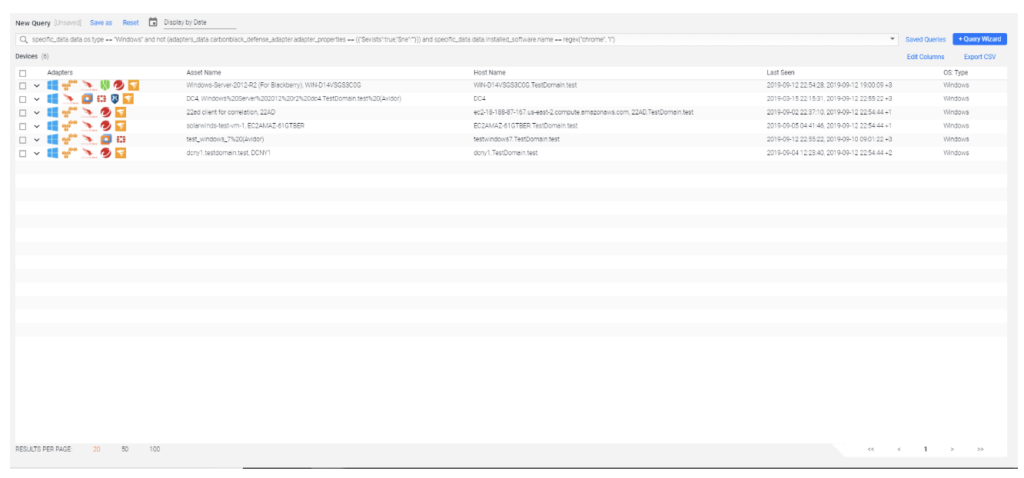
Great, so now we’ve got this list of non-compliant devices. What do we do with it?
This is where the “enforcement” part of our cybersecurity observability comes in. We’ve got four tricks up our sleeves:
And there you have it, folks! That’s how we turn the chaos of cybersecurity policy enforcement into a manageable, observable process. It’s not always pretty, but it gets the job done.
Remember this is just 1 out of 14 standard use cases we help our customers with as part of our CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More Concierge service. You can get that free!
Remember, cybersecurity is a team sport. We’re all in this together, trying to keep our digital worlds safe one device at a time. Some write the policies, others codify them to make them work. So, keep querying, keep enforcing, and most importantly, keep that sense of humor. You’re gonna need it in this field!
Stay safe out there, and may your false positives be few and your patches always successful!
Read the CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More documentation on Finding Devices Missing Endpoint Agents.