
Home » Latest Articles » CAASM Use Case #4 – Discovering Cloud Instances Not Being Scanned For Vulnerabilities

Welcome back, cloud security survivors! 🛟
We’re diving into the fourth instalment of our Cybersecurity Observability use cases series.
Today, we’re tackling a challenge that’s giving cloud security engineers nightmares: unscanned cloud instances.
Imagine this scenario: Your cloud infrastructure is growing faster than kudzu in summer. DevOpsDevOps is a partnership between software development and IT… More teams are spinning up instances left and right. Cloud engineers are Terraforming the hell out of your cloud accounts
Then, one late Friday afternoon, your CISO drops this bombshell:
"How do we know all our cloud instances are being scanned for vulnerabilities? What about the ones that pop up (and disappear?) between scheduled scans?" (Chief Information Security Officer)
Chief Security Officer
Yikes! It’s the cloud security equivalent of trying to hit an invisible moving target.
But don’t panic!
This is what SJULTRA can help you solve with CAASM (Cyber Asset Attack Surface Management) and cybersecurity observability.
Here’s the deal: Your vulnerability assessment tools are fantastic at finding issues on instances they know about. But cloud computing often cycles faster than your tools can keep up: new instances can pop up faster than you can say “DevOps.” These unscanned instances could be:
These invisible assets are like open doors in your cloud fortress. And the kicker? Your VA scanner won’t tell you about them because it doesn’t even know they exist!
Who's responsible to make sure cloud and ephemeral instances are correctly added to security frameworks such as vulnerability scans? Is it security? Or the person doing the deployment?
John Doe
This is where SJULTRA’s CAASM services, becomes your cloud security superhero. It’s like giving your security team x-ray vision for your entire cloud infrastructure.
CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More pulls data from multiple sources:
By cross-referencing these sources, we can spot the cloud instances that should be scanned but aren’t. It’s like finding needles in a cloud-shaped haystack!
Once we have CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More set up (remember, SJULTRA offers a free 30-day trial), we can start hunting those elusive unscanned cloud instances.
Want to find all AWS instances not being scanned for vulnerabilities?
Show me all AWS instances that aren't known to any Vulnerability Assessment Tools
John Doe
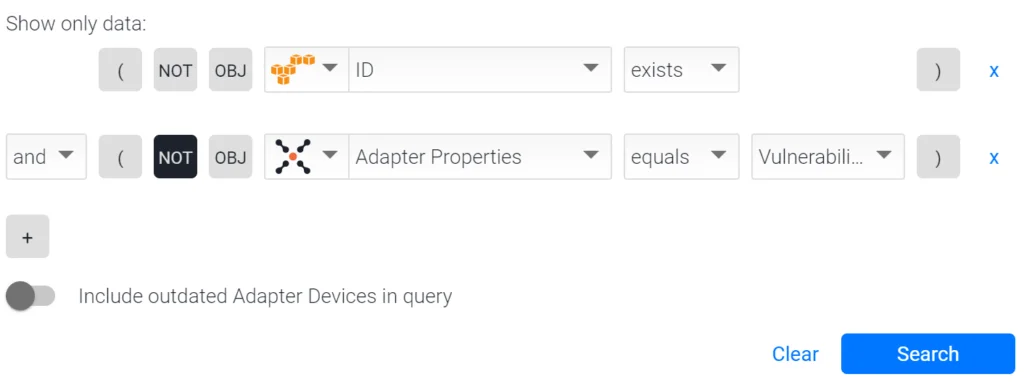
3. Query Languge (SQL):
(adapters_data.aws_adapter.id == ({"$exists":true,"$ne":""})) and not (adapters_data.qualys_scans_adapter.id == ({"$exists":true,"$ne":""}))
This query finds Amazon instances not being scanned by any tool categorized as a Vulnerability Assessment Tool.
The result set may be very large, so we can cull the list and prioritize the most urgent instances needing attention.
Here’s how to find just those AWS instances not being scanned that also have a public IP Address.
In the Query Wizard:
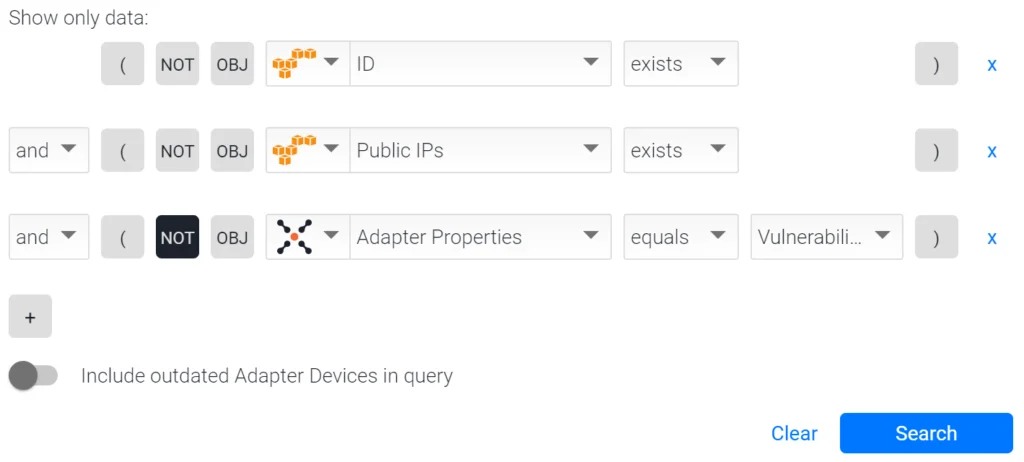
What about only AWS instances that have known Common Vulnerabilities and Exposures (CVE®) and are not being scanned for vulnerabilities?
AQL:
(adapters_data.aws_adapter.id == ({"$exists":true,"$ne":""})) and not specific_data.data.adapter_properties == "Vulnerability_Assessment" and (specific_data.data.software_cves.cve_id == ({"$exists":true,"$ne":""}))
This is a great example of extending and refining an AQL to build on the previous by only focusing on critical CVEs:
(adapters_data.aws_adapter.id == ({"$exists":true,"$ne":""})) and not specific_data.data.adapter_properties == "Vulnerability_Assessment" and (specific_data.data.software_cves.cve_id == ({"$exists":true,"$ne":""})) and specific_data.data.software_cves.cve_severity == "CRITICAL"
Great, we’ve uncovered these hidden cloud instances. What’s next? This is where the “action” part of our cybersecurity observability comes in. We’ve got four aces up our sleeves:
And there you have it, cloud security survivors!
That’s how we turn the elusive threat of unscanned cloud instances into a manageable, observable process. It’s not just about finding vulnerabilities; it’s about making sure we’re looking in all the right places, even as those places keep changing.
Remember, this is just 4 out of 14 standard use cases we help our customers with as part of our CAASM Concierge service. And guess what? You can get it for free!
What you don’t know can definitely hurt you in the cloud. But with the right tools and a bit of observability magic, we can keep those cloud instances in check.
Stay vigilant, keep querying, and may all your instances be scanned and secure!
Read the documentation: Finding Devices Not Being Scanned For Vulnerabilities.