
Home » Latest Articles » CAASM Use Case #13: Identifying and Prioritizing Vulnerabilities

Watch where you’re steppin’!
vulnerabilities are like hidden landmines scattered across your digital terrain. You know they’re there, but finding and neutralizing them before they cause damage? That’s the real challenge.
Welcome back, cybersecurity sleuths! 🔍
Today, we’re embarking on a mission that’s all about identifying and prioritizing those pesky vulnerabilities lurking in your environment. Think of it as being the Sherlock Holmes of cybersecurity—piecing together clues and outsmarting the adversaries before they strike.
So, grab your magnifying glass and notebook. Let’s dive into the twelfth installment of our Cybersecurity Observability use cases series, where we’re tackling how to expose and deal with vulnerabilities in your network.
Imagine you’re managing a massive fleet of devices—workstations, servers, IoT gadgets, you name it. Now, picture that each of these devices could be hiding a vulnerability, like a secret passage leading straight to your organization’s crown jewels. Scary, right?
Your mission, should you choose to accept it, is to identify these vulnerabilities, understand their impact, and prioritize them for remediation. But how do you even begin to map out this complex network of potential threats?
This is where SJULTRA’s CAASM services, becomes your incident response nitrous boost.
It’s like giving your security team a time machine and a crystal ball, all rolled into one.
CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More pulls data from a smorgasbord of sources:
By correlating this data, CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More creates a rich, unified view of your entire digital ecosystem. It’s like having a digital map of your entire IT landscape, with every device, user, and cloud instance clearly labeled.
Vulnerabilities come in all shapes and sizes, from software bugs to misconfigured firewalls.
The key to managing them effectively is visibility. And not just any visibility—comprehensive visibility that gives you a bird’s-eye view of your entire digital ecosystem.
CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More pulls data from a multitude of sources to create a single pane of glass for all observed vulnerabilities.
Whether it’s a CVE (Common Vulnerabilities and Exposures) with a critical severity score or a low-risk issue that’s been festering for months, CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More brings it all together. It’s like having a map that marks every potential hazard in your network.
With this unified view, you can see not only where vulnerabilities exist but also how they impact your business.
These insights are crucial for prioritizing your response and mitigating risks before they explode into full-blown incidents.
Once we’ve got CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More set up (remember, SJULTRA offers a free 30-day trial), we can begin the hunt!
To start the hunt, you’ll need to connect to the right data sources.
Here’s a quick rundown of the essential tools:
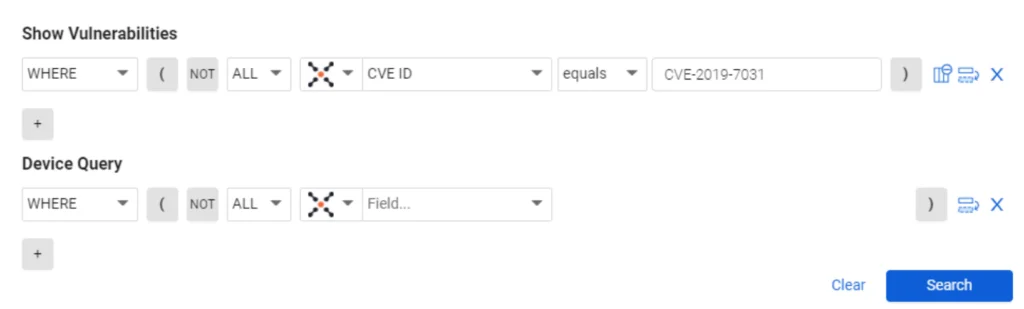
To identify all CVEs with a critical severity, in the Vulnerabilities section of the query, include criteria where CVE Severity equals CRITICAL.
CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More finds all critical vulnerabilities that exist in your environment, giving you data you can drill down into.
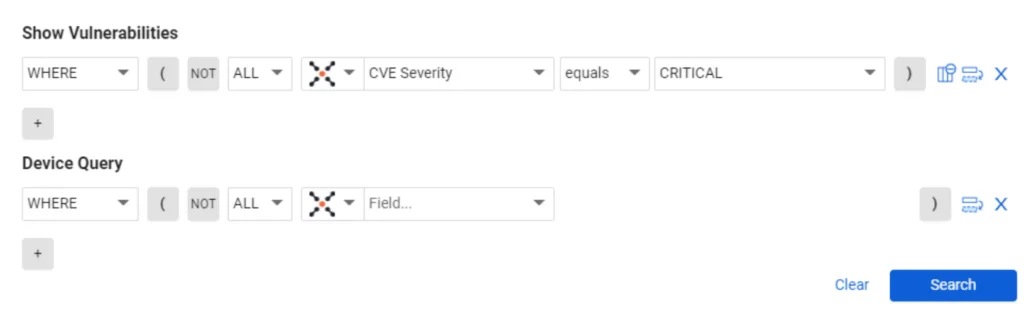
By building on the previous query, we can add a device parameter for Public IP to the query.
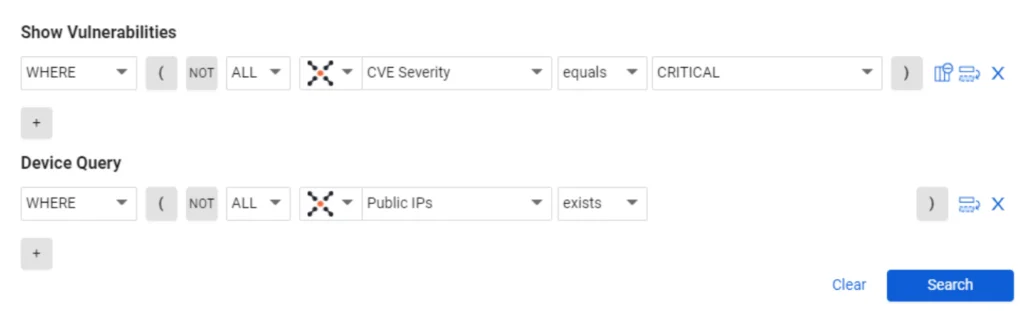
Using the Last Seen parameter of Vulnerabilities in the query wizard let’s you focus on new and old vulnerabilities.
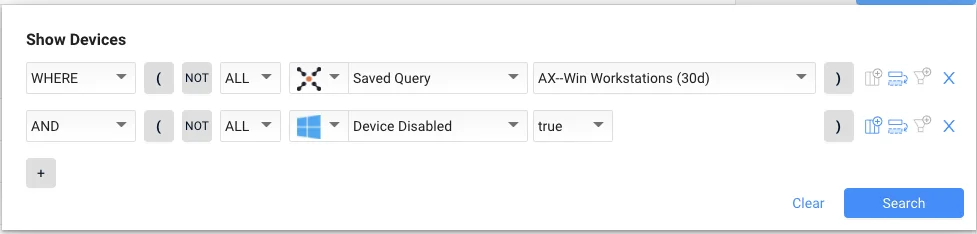
Persistent vulnerabilities are those that have existed in our environment for an extended period of time, creating a longer window of vulnerability and opportunity for exploitation. This is especially true if the devices impacted by the vulnerability are missing security agents.
In the vulnerability section of the query, include vulnerabilities where First Seen, Last Days is 60. Then add Device criteria where the Saved Query is Windows devices missing CrowdStrike agent.
NOTE: This using the really handy Saved Query feature of CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More, which means you can compose compound queries.
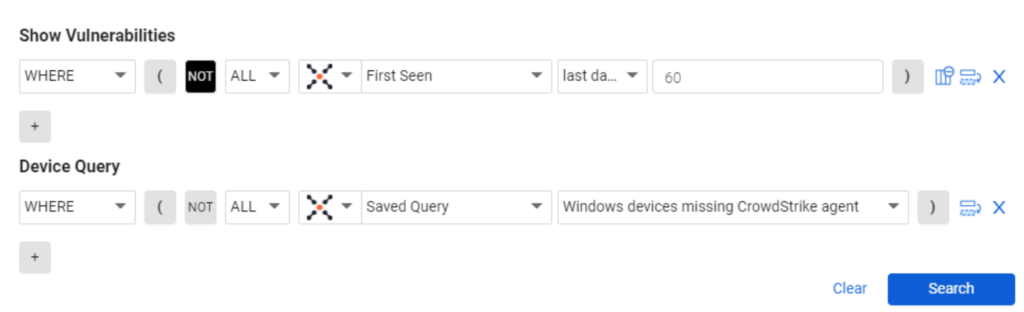
This is perhaps one of the most important CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More queries.
You can’t and shouldn’t panic over every CVE. If a CVE is critical but it’s only on one device that is high value or accessible, then it’s not a high priority.
This is like the fire extinguisher step.
The idea is this:
Again, this is using composable compound queries.
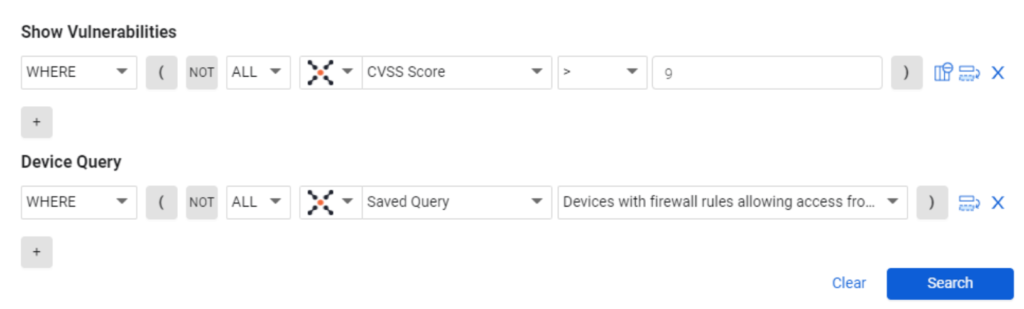
Great, we’ve uncovered these hidden digital fossils. What’s next? This is where the “action” part of our cybersecurity observability comes in. With CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More, we’ve got four aces up our sleeves:


And there you have it, new sleuthing tools and practices! 🏺
If you create these queries and automate enforcement, then you’ve got protection as you sleep.
And if something bad DOES happen, then you can quickly find the information to either soothe your brow or set a fire under your… you get it!
And don’t forget our no catch, no cost, no obligation, limited time free CAASM trial offer.
Read the CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… More documentation: Identifying and prioritizing vulnerabilities